Adaptive security is traditionally a network security model to accommodate for the increasing complexity of threats targeting the network of organizations. Intrusion Detection Systems, for example, are one application of adaptive security and use a heuristic system that correlates information to make recommendations rather than using hard blocking rules as a Firewall does.
Generally, Adaptive Security is an approach to cybersecurity that analyzes behaviors and events to continuously assess risk and automatically provide proportional enforcement that can be dialed up or down.
I suggest this model to adopt the transaction security features for an imaginary online bank.
Traditional Transaction Security in Banking
Financial information is surely near the top of the list of all the things people want to keep safe. The login to the online system of a bank is usually only protected by username (identification) and password (authentication) and gives access to the account in a read-only mode. Past transaction and account information can only be looked at.
The second layer of security (two-factor authentication) is necessary once the user intends to do an online change to the account. This change could be a new standing order, a money transaction, or the change of the address.
Additional authentication methods vary from bank to bank and include one-time passwords from a tan list (classic TAN), SMS or push notifications to mobile devices (mobileTAN or pushTAN), or the use of a device to create the TAN (cardTAN or chipTAN).

Adaptive Transaction Security
I want to suggest a security model where the frequency of interaction between people can be used to remove the enforcement of a second factor for future transactions between those people. This model is improving the usability for the customer while it manages the risk of fraud for the bank.
A malicious player who hacks the account could not benefit from the removal of 2FA for those transactions because it would only whitelist accounts with a strong transaction relationship.
Graph Database
Graph Databases allow to represent related data as it is as a set of objects connected by a set of relationships. Graph theory dates back to 1735, when Leonard Euler solved the Seven Bridges of Königsberg problem by devising a topology consisting of nodes and relationships.
In computing, a graph database uses graph structures for semantic queries with nodes, edges, and properties to represent and store data. A key concept of the system is the graph (relationship). The graph relates the data items in the store to a collection of nodes and edges, the edges representing the relationships between the nodes.
Graph databases, by design, allow simple and fast retrieval of complex hierarchical structures that are difficult to model in relational systems. A graph is essentially an index data structure. It never needs to load or touch unrelated data for a given query. They’re an excellent solution for real-time big data analytical queries.
Let’s look at some example transactions between four people. Each customer and transaction is an object and the transaction flow is represented by a graph.
_:bob <first.name> "Bob" .
_:alice <first.name> "Alice" .
_:chuck <first.name> "Chuck" .
_:rudi <first.name> "Rudi" .
_:bob <sends> _:tn1 .
_:alice <receives> _:tn1 .
_:bob <sends> _:tn2 .
_:alice <receives> _:tn2 .
...
_:bob <receives> _:tn19 .
_:alice <sends> _:tn20 .
_:bob <receives> _:tn20 .
I inject the data into dgraph and visualize the amount of nodes (transactions) between people:
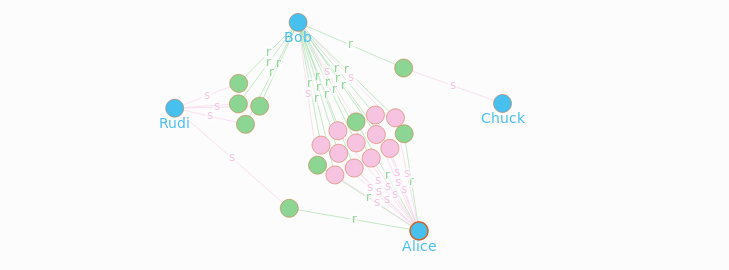
We can see a strong relationship between Alice and Bob. Alice is sending money on a regular basis to Bob. We could suggest her to remove 2FA when initiating new transactions to Bob. A more advanced data model with additional parameters, like the transaction value and the date, would help to consider only certain transactions between Alice and Bob.
Conclusion
Historically, effective security came at the expense of usability and vice versa. Today we have technologies that present the user with appropriate security solutions to match the task, risk, and real world scenario. Organizations need to start looking at the historical data and use it to tailor security around it. Smart risk management models can be applied to benefit the user.
Nobody will question strong authentication when a first-time transaction is made to a vendor in a foreign country. But having the same requirements whenever sending money to siblings, parents, or friends just doesn’t make any sense. Using the frequency of interaction with other people can help to accomplish security features that adapt to the situation.