Security risk assessments identify, quantify, and prioritize risks against defined criteria for risk management and objectives relevant to the organization.
Risk is a consequence of an action taken and can have a positive or negative outcome. It can be managed in 5 distinct ways.

Accepting a risk means there are no actions. This is a valid approach but requires identification and documentation of the risk. The acceptance of a risk has to be done by a qualified person. Real-life example: Smoking, drinking or base jumping
Avoiding is a change of plans and not executing on a strategy, investment or software project because of the risk. Real-life example: Stick to the speed limit, not go bungee jumping
Transfer of risk means another party, person or organization is taking the risk instead. Real-life example: insurance industry
Mitigation against a risk is the most common approach. One can mitigate against the impact and or mitigate by reducing the likelihood. Real-life example: audits, backup, redundancy, error-tolerant design
Exploiting is an option if the risk has a positive impact. Looking for ways to increase the likelihood and/or impact of a risk. Real-life example: using new technologies
All mentioned risk management approaches rely on a prior assessment. The assessment of the risk for an organization has to follow a structured approach. Risk assessment and management is an essential part of security management. Security assessment methodologies like CRAMM contain risk assessment modules. Risk assessment methodologies like Mehari have evolved to be security assessment methodologies. A systematic approach to security risk assessment is necessary to identify security requirements and to create an effective Information Security Management System (ISMS){:target=”_blank”}.
Security risk assessments identify, quantify, and prioritize risks against defined criteria for risk management and objectives relevant to the organization.
When to run Security Risk Assessment
Whenever a new system, software, process or partner is connected to the organization. It’s essential to understand for example what data is shared and which privileged rights are implemented. A decision has to be made conscious and has to be aligned with the risk profile of a company. Existing assessments have to be revisited on a regular basis to adapt to the ever-evolving security threat landscape.
Each risk assessment has to be tailored to the subject of the assessment.
Stories from the trenches
- A designer finds this new productivity tool on the internet and installs it on the company notebook. The tool turns out to be malware.
- A manager is doing a test run with a new vendor and shares production data that turns out to include privacy protected data. The vendor is in a territory not bound to EU privacy laws and does not comply with GDPR
- Development teams use third-party modules for a software project. One module has malicious code injected (software supply chain attack)
- A company decides to go global without a global security framework. Later a foreign branch is hacked and the HQ is affected.
Example Cyber Security Risk Assessment
A bank is evaluating a new Customer Relationship Management (CRM) system. The new system is a browser-based SaaS (Software as a service) solution. The new CRM software is part of a digitalization project in the bank with the purpose to reduce costs and improve customer relationship. The vendor of the SaaS solution was successfully approved after a vendor risk assessment. The contract with the SaaS provider includes SLA definitions and SLA monitoring metrics.
We scope this risk assessment to only look at the Data, Network and Client. People and Client hardware availability has to be covered in a disaster recovery plan and according to corporate security requirements. Customer and Support Agent interaction has to follow security approved processes.
Step No. 1: Identify Assets and define the scope
The identification of the assets can includes hardware, software, data, and personnel. It’s important to work with business users and management to create a list of all valuable assets. A tech person might not have all the information necessary to identify the assets or potential consequences.
It’s possible to define the scope of the assessment and recommend further assessments.
Step No. 2: Identify potential consequences
Determine what financial and reputational losses the organization would suffer if a given asset were damaged. This will later be used to determine the impact of loss or unavailability of an asset.
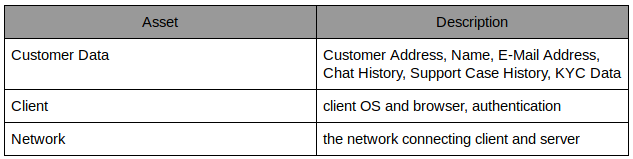
Customer Data As a financial institute the partial or complete loss of customer data has legal implications and has to be reported to the authorities. The reputational consequences are a loss of trust in the organization. A full or partial data breach has legal, reputational and financial implications.
Client Because of the SaaS solution the agents only require a browser. Browsers have evolved into cloud-based password managers and provide access to extensions.
Network A stable network connection with low latency is required for the SaaS solution to work. Loss of the connection means downtime for the customer support department which implies reputational consequences. Prolonged downtimes will have financial impact on the organiziation.
Step No. 3: Identify Threats
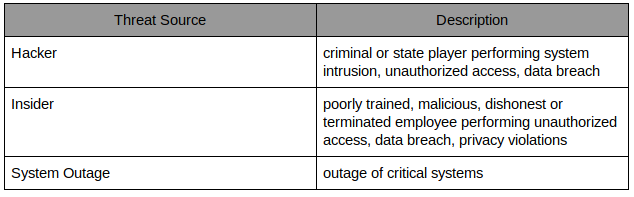
A threat is anything that might exploit a vulnerability to breach your security and cause harm to your assets. Threats are specific to the company and derive from the company threat assessment. A bank of a certain size is considered critical infrastructure and is facing threats from computer criminals and state players. Natural disasters are also considered a threat but out of scope for this assessment.
Step No. 4: Identify Vulnerabilities
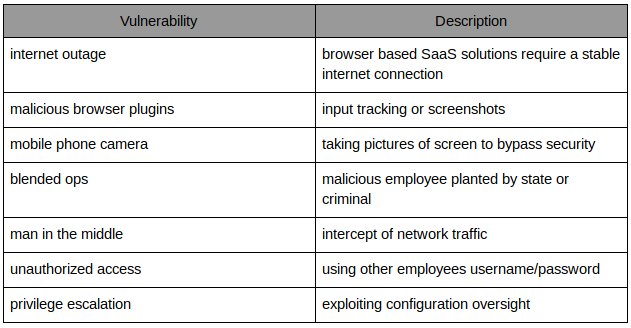
This step is probably one of the most challenging aspects of the security risk assessment. Vulnerability analysis requires technical understanding, up to date knowledge about the security threat landscape and the ability to tie it all together on the use case. I am giving some examples here without claim for completeness.
Step No. 5: Assess the risk
Risk is the potential that a given threat will exploit the vulnerabilities of the environment and cause harm to one or more assets. It is important to document the justification or rationale for each impact assessment and probability of occurrence rating. If the conditions or environment change, the assessment might need to be revisited. The rationale helps to communicate the significance of the risk.
Risk = Threat Likelihood x Magnitude of Impact
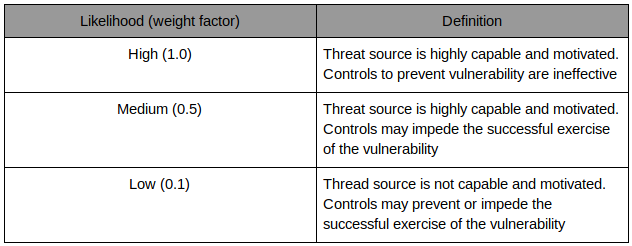
The likelihood of an event to occur can be defined by factoring in the capability and motivation of a threat and the existing controls to prevent a threat.
The definition of the impact by the value of the data or service and the impact a loss has for the organization.
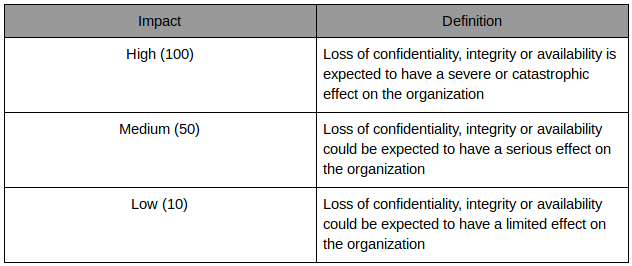
Risk model
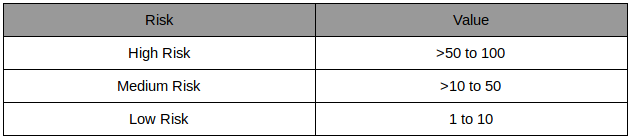
The resulting risk management plan
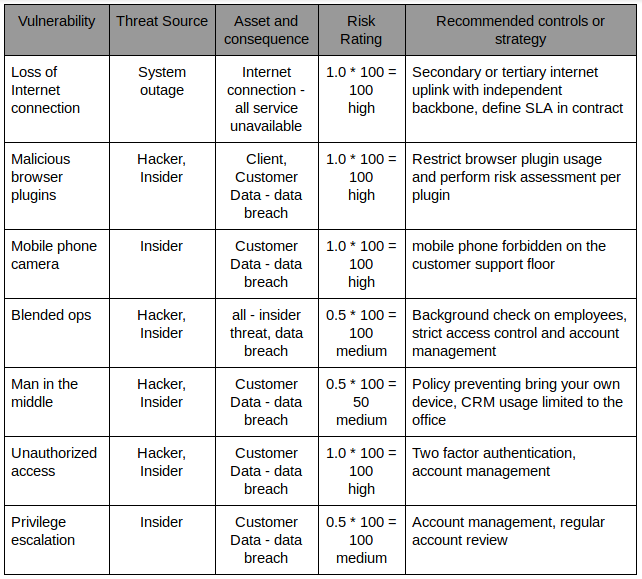
With this simplified risk assessment we can now decide on how the risk is managed. Most organizations will try to mitigate the risk and quantification helps to justify the costs.