Cloud computing has been one of the most disruptive technologies in the last decade. Unprecedented flexibility, scalability, and cost-effectiveness seduced organizations to equate digital transformation with cloud migration.
But in 2020, the bright future of cloud computing darkened when the EU Court of Justice (CJEU) invalidated the transfer deal “Privacy Shield”, the legal foundation on which EU companies outsourced to US cloud providers.

This so-called Schrems II ruling leaves many companies in an awkward situation. US cloud providers are mostly no help and retreat to mere lip services.
No false conclusions should be drawn from the supposed inaction of the data protection authorities. In the case of the USA in particular, the CJEU’s ruling has given the supervisory authorities clear guidelines that leave little room for discretion.
In this article, we describe technical measures that organizations can take to continue the use of US cloud providers post-Schrems II.
TL;DR Schrems II & US Cloud Act
Large US companies, such as Microsoft, Amazon, or Google, advertise that they have an EU subsidiary with server locations in Europe, which means that no transfer to the USA would take place.
However, the Schrems II ruling states that a server located in the EU does not protect against US laws: The CLOUD Act authorizes US authorities to access data stored by US service providers and their subsidiaries outside the USA - even if this represents a conflict with local national law.
The CJEU notes that data protection standards, in general, cannot be guaranteed when outsourcing to US providers. US law is incompatible with the requirements of EU consumer rights.
Under the GDPR, EU businesses have to prevent unauthorized access to personal data. What’s new about Schrems II, however, is that this time we do not have to fear hackers or human error, but American law enforcement. The cloud environment has become hostile territory.
Let’s look at some technical safeguards for the post Schrems II era.
Assessment And Classification
The first task, in any case, is an honest evaluation of the situation to plan for supplementary measures.
- What cloud providers are used?
- What processes are outsourced to the provider?
- Which laws apply to the service provider?
- Is the privacy and security policy appropriate?
- What type of data is transferred?
- Do we need a data processing agreement?
Organizations are well-advised to maintain a detailed list of suppliers and sub-suppliers. The full outsourcing chain has to be considered. For example, an EU-based HR software provider can potentially run on a US infrastructure service (IaaS).
Anonymization
Completely anonymized data is not protected by the GDPR and can consequently be transferred to US cloud providers. The challenge is to preserve the usability of such anonymized data.
OpenSource tools such as ARX are very helpful in building proper documentation and help businesses to strike the right balance between anonymization and data usability. Proof for the anonymization must be defendable against objections from data authorities.
Smart Clients
We have written a whole article on this topic here: Shift To The Client. Smart Client architecture emphasizes the client over the backend when it comes to the processing and storage of personal data.
This approach has, for example, been chosen for the official German COVID-19 contact tracing app. The app is not supported by a centralized storage system and anonymized data is only shared when a warning to other users is initiated.
Decentralized architecture and smart clients are a much too rarely considered possibility when planning for a business case. With Schrems II, however, the traditional client-server architecture will be a challenge in the future.
Provider Independent Encryption
Cloud providers make key management easy to use with integrated services. But this doesn’t address the underlying issue of Schrems II since the key ownership stays with the cloud provider and therefore enables the provider to decrypt any sensitive data in transit or storage.
Provider independent encryption (or key management) on the other hand is a suitable approach to prevent unauthorized access. Organizations with such a system can effectively block cloud providers from reading sensitive data.
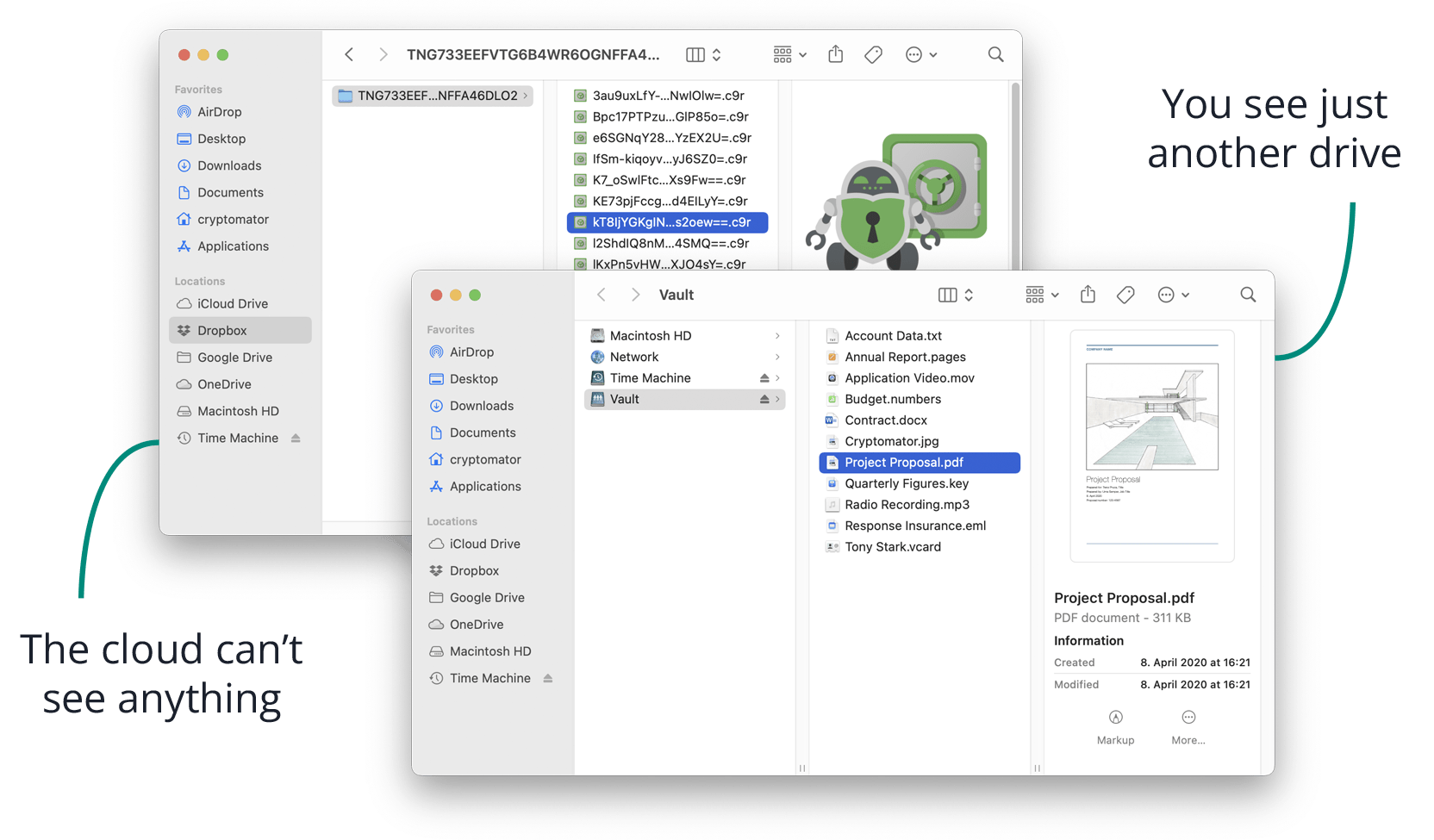
A great solution for cloud storage solutions like Google Drive or Dropbox is the usage of key management services like Cryptomator or Boxcryptor. These tools hide the content of files from the storage provider by implementing full end-to-end encryption (e2ee).
Conclusion
We have highlighted some technical ideas that can serve as a starting point for a cloud outsourcing approach in line with the GDPR. However, the most important question is if every single outsourcing project needs to be done with a US provider or whether there is not a suitable EU solution.
Choose your battles carefully. The days of pragmatically transferring data to vendors and configuring something that somehow worked are over.
The future of outsourcing to the cloud lies in the deliberate planning of processing activities and supplementary measures to secure a run-of-the-mill cloud service.