Security is a major concern for all software products. Introducing security activities into the development process can be a challenging task. To be successful, close integration with existing processes is essential to embed the new tasks seamlessly into the tried and tested processes.
The Open Web Application Security Project (OWASP) has developed a useful framework for this purpose in the form of the Software Assurance Maturity Model SAMM. It enables companies not only to measure the maturity of their software development processes in terms of security but also to iteratively improve.

The v2 SAMM
Maturity Model
The current version of the model (v2) is based on a set of 15 security practices grouped into five core areas of business functions. Governance, design, implementation, verification, and operations.
Based on a detailed catalog of questions, companies can determine their maturity level not only per individual activity but also aggregated to the respective areas and the entire development process.
In addition to the evaluation of the actual situation, an evaluation of the maturity development over time can be presented, which enables the visualization of the project progress and a comparison with the targeted milestones.
The maturity model is agnostic in terms of techniques and development methodology, but a certain affinity to agile development methods cannot be denied.
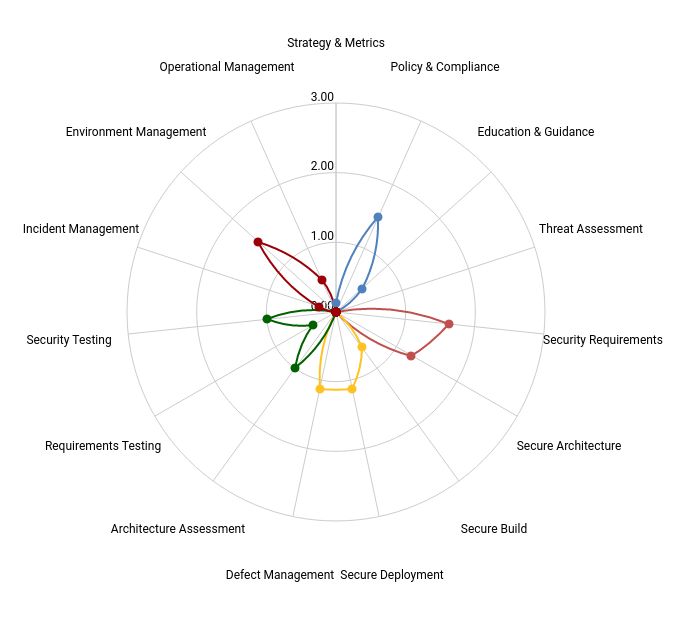
Initial maturity graph for a startup
Governance
The governance chapter aims at key performance indicators (KPIs) which enables teams to see if they have achieved the targeted progress and where intervention is required.
Additionally, it covers the policy and compliance of projects and the suppliers of third-party components.
Well-trained and motivated employees are a key factor for a successful security program. These security champions are not only characterized by their interest and knowledge in the security topic but are also communicative and actively contribute to a positively reinforced security culture.
Design
The security activities in the design phase involve defining security requirements, creating a security architecture, and performing threat modeling.
The goal is to find out what threats are affecting the application being developed and whether they are being handled appropriately.
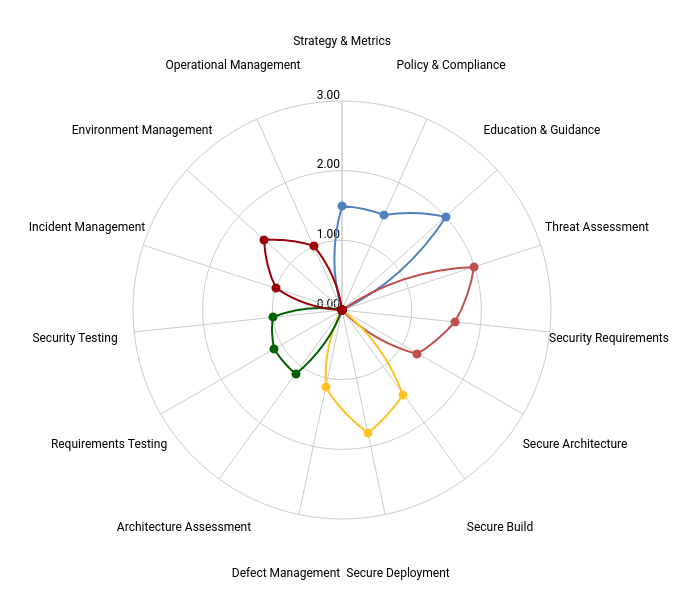
Balanced medium maturity
Implementation
In this chapter, SAMM focuses on the tools to integrate security into the build and deployment process.
Questions address the secure handling of credentials to minimize human involvement during initial setup and the subsequent renewal of secrets.
While being important throughout the development lifecycle, the management of defects is also handled in the implementation questions.
Verification
Promoting software into the production environment without prior quality assurance has become unthinkable in many areas. This applies in particular to security checks.
The chapter recommends security checks that are based on concrete security requirements but generic tests still have their justification.
SAMM places a emphasis on denial of service benchmarks, fuzzing, regression testing for fixed vulnerabilities, and test automation in the build and deployment process.
It is important not to lose sight of the appropriateness of the tests for the specific application criticality.
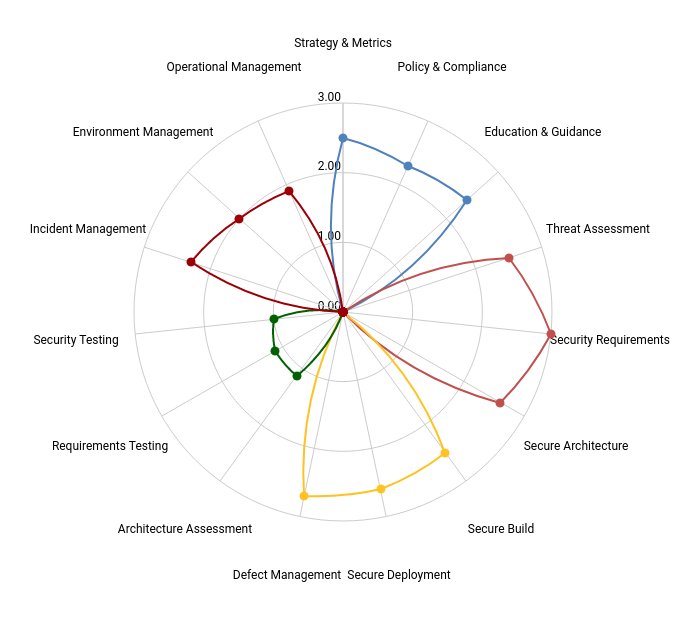
Solid maturity with a opportunity for improvement in the verification section
Operation
With DevOps, the boundaries of the software development process are increasingly beginning to blur. The maturity model adds a separate section for operation.
The specifications tolerate manual log analysis, ad hoc responses to incidents, and best efforts to detect attacks at a low maturity level. Improved maturity requires a dedicated incident response team and defined processes for the detection and remediation of incidents.
Patch management and configuration hardening have clear recommendations for regular and systematic activities across the entire technology stack.
The highest score points in SAMM require the rapid decommissioning of outdated applications or strategies to monitor such systems until they are replaced with modern successors.
Summary
OWASP SAMM provides a reliable framework for improving the software development process. Teams should start with an initial maturity assessment to get the status quo. From there, a roadmap can be created that defines the target picture and milestones along the way.