Each month we gather our favorite finds from around the internet and recommend them to you right here. So go ahead, pour yourself a cup of coffee, or tea, and settle in.
GitHub shares vulnerability database with community
The GitHub Advisory Database is the world’s largest database for recording security vulnerabilities in open-source software. A team maintains this data full-time. The database is used, among other things, for security checks of the package managers npm and NuGet as well as for GitHub’s Dependabot warnings. >read<
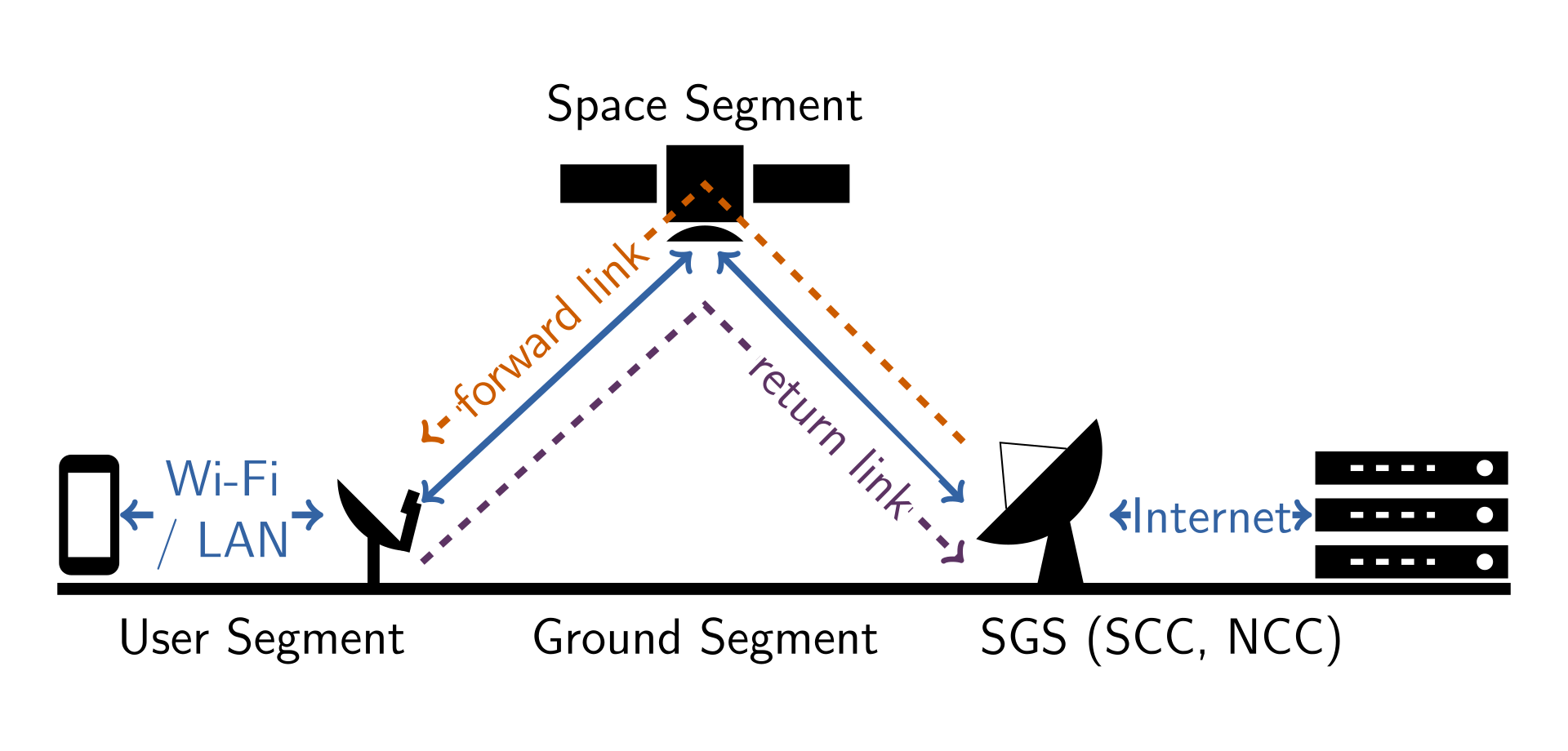
SATCOM terminals under attack
Parallel to the Russian invasion of Ukraine, thousands of KA-SAT terminals stopped working in several European countries. Remotely operated wind turbines, connected via SATCOM link, lost contact with their servers as a result. Ruben Santamarta analyses the publicly available information in his interesting article. >read<
Critical vulnerabilities in APC Uninterruptible Power Supply
Armis has discovered three critical vulnerabilities in APC Smart-UPS devices. These are of course controlled through an internet connection nowadays. A malicious actor can use TLS bypass and TLS overflow to gain unauthenticated access to the UPS and use the device for further lateral movement in the network. >read<
Pro-tips for BurpSuite
Burp Suite is a network analysis toolbox for testing web applications. It includes a proxy, which intercepts HTTP/HTTPS traffic and modifies the HTTP headers before sending the data to the server. The article by N00PY gives great tips for the powerful software. >read<
Famous npm package deletes files to protest Ukraine war
The importance of supply chain security for open source components in business code has been highlighted once again this month. The developer of the npm module node-ipc.js added malicious code to it that deletes files if the software thinks it is on a Russian or Belarusian system based on a geo-location IP determination. The incident has drawn sharp criticism from the open-source community for actively deploying destructive payloads in a popular library without any warning to honest users. >read<
NSA hardening guide for Kubernetes
The biggest sources of compromise in Kubernetes are supply chain risks, malicious threat actors, and insider threats. The NSA guide describes the security challenges associated with setting up and securing a Kubernetes cluster and provides strategies to avoid common misconfiguration and implement hardening measures. >read<
Escaping privileged containers for fun
Jordy writes on his blog about discovering an escape from a privileged container via the kernel’s coredump handling code. Interesting read and let’s all agree to not run privileged containers, not even for fun! >read<