Dig into a selection of the best articles, code, and projects we found this past month.
Massive Data Breach in China
The personally identifiable information (PII) of one billion people in China has been put up for sale on the darknet. The dataset was reportedly extracted from an unsecured Shanghai police database hosted on Alibaba’s cloud hosting platform. There have been countless instances where organizations have similarly exposed sensitive data by leaving it poorly secured. What makes the Shanghai breach notable is its sheer scale. By most accounts, it is one of the largest ever known compromises of PII. >read<
Threat Modeling Field Guide
A solid guide to a multitude of threat modeling methodologies has been published on shellsharks. Each of the methods comes with a solid description and visualizations. The Appendix goes into data flow diagrams and tooling to perform the perfect threat modeling session for your use case. >read<
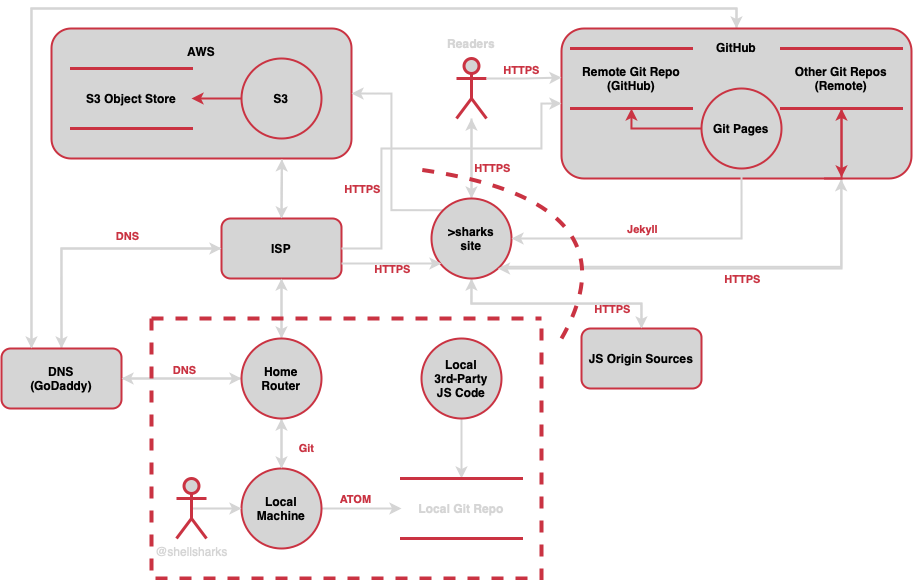
Data Flow Diagram
Binary Vulnerability Toolset With Ghidra and Semgrep
Marco Ivaldi released a technical article about automated vulnerability discovery via static analysis techniques. The walkthrough covers custom scripts for semgrep and ghidra to build a toolset for binary bug hunting. >read<
HackerOne Employee Steals Vulnerability Reports for Personal Gains
A HackerOne employee has been fired for collecting bug bounties from its customers after alerting them to vulnerabilities that were found by other researchers and shared privately with HackerOne through its vulnerability disclosure program. >read<

Hackers
NIST Announces First Four Quantum-Resistant Cryptographic Algorithms
Security experts have warned that practical quantum computers could break many of today’s popular encryption algorithms, such as RSA and elliptic curve cryptography. On July 5, the National Institute of Standards and Technology (NIST) announced the selection of four candidates to form the basis of future data-protection technologies able to withstand attacks from quantum computers. >read<
Most Of The Domains in Australia Have Security Issue With Their SPF And DMARC Configuration
Sebastian Salla scanned 1.7 million Australian domains and checked for various types of SPF & DMARC-related issues. His interesting writeup describes how he ran 400 concurrent lambda functions for 24 hours and reveals the less than optimal results from his scan. >read<
Unlock Honda cars remotely
A team of security researchers found that several modern Honda car models have a vulnerable rolling code mechanism that allows unlocking the cars or even starting the engine remotely. Called Rolling-PWN, the weakness enables replay attacks where a threat actor intercepts the codes from the keyfob to the car and uses them to unlock or start the vehicle. >read<
Time To Patch Before Scan: 15 Minutes
There is less time to patch disclosed security vulnerabilities than previously thought, as a new report from Palo Alto’s Unit 42 shows. Threat actors scan for vulnerable endpoints within 15 minutes of a new CVE being publicly disclosed. The speed at which actors target devices and systems only adds additional pressure on security teams that already struggle to get vulnerabilities managed. >read<