The ATT&CK (Adversarial Techniques, Tactics, and Common Knowledge) framework is an open-source threat intelligence knowledge base designed to equip organizations with the information they need to defend their networks against sophisticated cyber threats.
Developed by MITRE Corporation and a community of security experts and practitioners, ATT&CK provides a comprehensive view of attack tactics and techniques across all stages of the adversary lifecycle.

Usage
Companies can use the ATT&CK framework to gain better visibility into the tactics, techniques, and procedures adversaries use to attack their systems. By understanding the various stages of the attacker lifecycle, organizations can build more effective security defenses and incident response plans.
The ATT&CK framework can also be used to prioritize and validate detection logic. Companies can review techniques and tactics used by adversaries in past attacks and develop rules and use cases based on that information. This can help ensure that detection logic is focused on the most pressing security risks. Additionally, companies can use ATT&CK to better understand the tactics and techniques used by threat actors, which can help inform their security investments and plans.
Attack Lifecycle
ATT&CK divides attack tactics into nine stages based on real-world observations of attackers:
-
Initial Access covers techniques used to gain access to the target system
-
Execution describes how adversaries establish a foothold after gaining access
-
Persistence relates to how attackers maintain their presence on the system
-
Discovery covers the approach used to identify assets and vulnerabilities in the system
-
Lateral Movement represents procedures used to move across the network
-
Collection describes how attackers extract data from systems
-
Command and Control relate to techniques used to control compromised systems
-
Exfiltration covers techniques used to transport data out of the system
-
Impact describes the ultimate objectives of the attack
The relationship between tactics and techniques can be visualized in the ATT&CK Matrix.
For example, under the tactic Reconnaissance, there are a series of techniques including Active Scanning or Gather Victim Org Information. Each of these is a single technique that attackers may use to achieve the goal of reconnaissance.
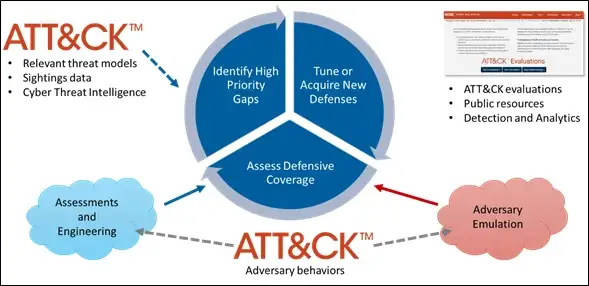
Getting started
MITRE has released a great series of getting started blog posts. Organizations can use ATT&CK to prioritize and validate detection logic by analyzing techniques used by adversaries in past attacks. With this knowledge, organizations can start developing rules and use cases to better protect their networks against sophisticated threats.