The “Universal 2nd Factor” is one of the most secure authentication methods currently available. Its advantages are based on hardware isolation and modern cryptography.
U2F is an open standard that improves and simplifies traditional two-factor authentication. It is utilizing a Universal Serial Bus (USB) or near-field communication (NFC) device to achieve secure authentication and was initially developed by Google and Yubico.

OTP
One-time passwords (OTP) or time-based one-time passwords (TOTP) provide a relatively secure second factor to millions of users. The popularity and good propagation are related to the simplicity of the concept. But there are shortcomings to this method.
So what is 2FA OTP? In addition to a static user name/password credential, a user adds another authentication factor - one that is dynamically generated. By definition, this OTP credential is only valid for one login before it becomes obsolete.
OTP technology is compatible with all major platforms (desktop, laptop, mobile) and even legacy environments. It is the most popular choice among second-factor protocols.
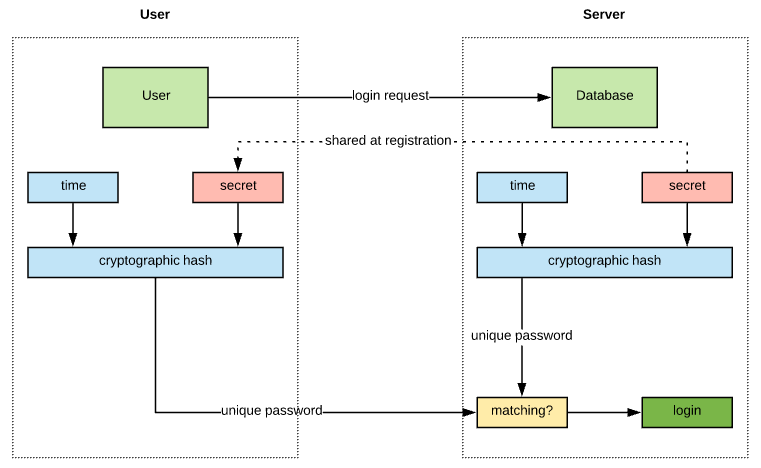
One-time credentials are delivered in different ways, usually via a physical object, such as a mobile phone (using SMS or an app), a token with an LCD-display, or a YubiKey. Concrete OTP algorithms vary greatly but they have one thing in common: a shared secret between client and server.
TOTP implementations, like Google Authenticator, require time-synchronization and a shared secret between the authentication server and the device providing the password.
Second-factor one-time passwords offer protection against password replay but it’s not designed to counter a man-in-the-middle or phishing attack. The shared secret between client and server is the main weakness of OTP and TOTP.
A theoretical attack is quite simple: token codes or shared secrets can get intercepted during authentication or stolen during the initialization of OTP. This is significant since it is the principal threat most users believe they are solving with this technology.
U2F
U2F improves on OTP vulnerabilities such as phishing and man-in-the-middle attacks by implementing a real-time challenge-response scheme with public-key encryption and digital signatures.
When a user registers a U2F device with an online service, a public/private key pair is generated on the client and the public key is shared with the server.
After registration, when the user attempts to log in, the service provider sends a challenge to the client. The client compiles at least the information about the source of the challenge into the response and signs it with the private key before sending it back to the server.
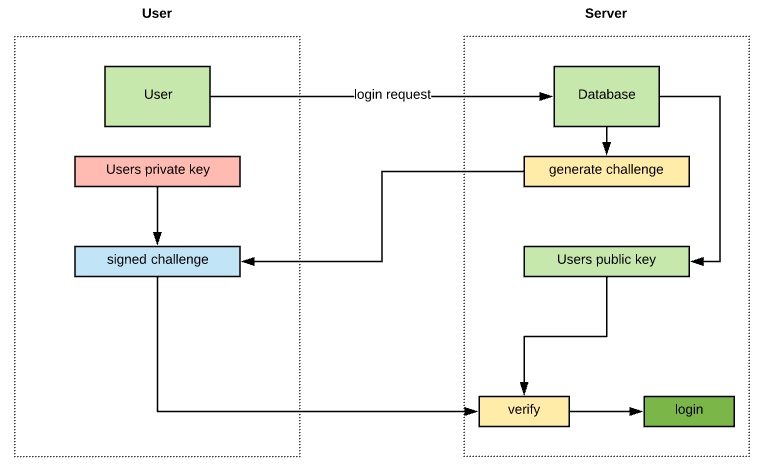
The server can detect an abnormality in the response (since it is issuing the challenge) and deny the transaction if a rogue site or middle-man manipulates the flow.
U2F is resistant to phishing by design too. For instance, the user cannot be tricked into pressing the key and authenticate with a “fake” web page since the authentication origin is part of the process and the communication between the device and the web browser. A malicious person cannot ask for your “U2F codes” because there are no codes in play.
The future…
Nowadays most people use biometrics-based methods for authentication on personal mobile devices to unlock them. Fingerprint and facial recognition have been around for a while now but they’re not exactly foolproof. It’s possible to trick fingerprint sensors and basic facial recognition systems.

Since most consumer OTP solutions are depending on mobile phones as the second factor, it opens up the question of future dependability of this system.
U2F devices, on the other hand, will become cheaper and more commonly accepted by service providers. I predict a future of adaptive security with many potential factors for authentication. Shared secret knowledge, physical ownership of a secure device, location, and behavior are all factors, that if combined, will convince machines that we are who we say we are.