The Internet Protocol Suite is commonly known as TCP/IP because of the central protocols in the suite: Transmission Control Protocol (TCP) and Internet Protocol (IP).
TCP/IP is the foundation of all global internet communication and dominates networks around the world. The technical standards are maintained by the Internet Engineering Task Force (IETF).
The Internet Protocol Suite predates the OSI Reference Model which is a more comprehensive framework for general networking systems.
TCP/IP originates from research conducted by DARPA in the 1960s. The design included a fundamental change to existing protocols as the network would only provide functions to efficiently transmitting and routing traffic between end nodes and that all other intelligence would be located at the edge of the network. This design is known as the end-to-end principle.

In 1982 the US Department of Defense declared TCP/IP as the standard for all computer networking and Universities followed in the same year. The promotion of the protocol by large corporations like IBM and DEC led to increasing commercial use.
The dominance of TCP/IP as the standard for network communication was cemented when the University of California, Berkeley placed the TCP/IP code developed for BSD UNIX into the public domain in 1989. More and more vendors included the code in commercial software releases and more people joined Internet protocol suite based networks.
Layers of TCP/IP
The defining specification of the suite is found in RFC 1122 and RFC 1123. A four-layer model is outlined as follows.
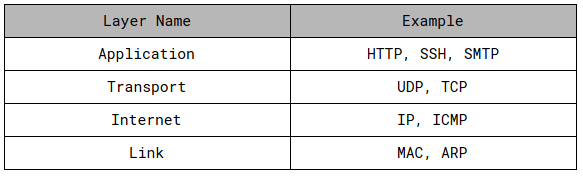
Application
In this layer applications or processes, create user data and communicate this data to other applications on the same host or a remote one. The applications make use of the services provided by the underlying lower layers, especially the transport layer which provides reliable or unreliable communication protocols to other processes. Application architecture is characterized by the client-server model or peer-to-peer computing. This is the layer in which all application protocols, such as SMTP, FTP, SSH, HTTPS, operate.
Transport
The transport layer performs host-to-host communication on local or remote networks. The two primary protocols in this layer are the simplex connectionless UDP or User Datagram Protocol and the full-duplex connection-oriented TCP or Transmission Control Protocol.
Data exchange between two systems on this layer is performed via ports. Both TCP and UDP support 65536 ports which are just an address number that both ends of the communication link agree to use when transferring data on the transport layer. A single IP address can support multiple simultaneous communications by utilizing multiple ports.
Let’s look at TCP which is connection-oriented and performs a handshake process to establish a communication session. The three-way-handshake is a prerequisite for data transmission between server and client and goes as follows:
The client sends a SYN (synchronize) flagged packet to the server. The server responds with a SYN/ACK (synchronize and acknowledge) flagged packet back to the client. The client sends an ACK (acknowledge) flagged packet back to the server.
There are two methods to disconnect a TCP session once a communication session is complete. The most common one is to use a FIN (finish) flagged packet which both sides of the communication have to send once all data is transmitted. The other side has to reply with an ACK flagged packet. It takes 4 packets to gracefully shut down a TCP session.
The alternative disconnect method is to send a RST (reset) flagged packet, this causes an abrupt and immediate termination of the session.
UDP, the other player in the transport layer, is a connectionless best-effort protocol and offers no error detection and correction. It also doesn’t require a pre-established session and is therefore considered unreliable. With its low overhead, it can transmit data quickly but should only be used for non-essential data delivery.

Internet
The Internet Protocol or IP operates on the Network layer of the OSI Model. IP provides route addressing for data packets and it is this route addressing that makes TCP/IP the foundation of global internet communications because it provides a way to identify and prescribe transmission paths.
The Internet Protocol is connectionless and acts as an unreliable datagram service. It doesn’t guarantee that packets are delivered in the right order or tht they are delivered at all. Only when TCP and IP work together a reliable and controlled communication session is established.
IPv4 is the most widely used version of the Internet Protocol. A new version known as IPv6 is being adopted for private and public network use and offers new features and new challenges for Administrators and Security Engineers.
ICMP or Internet Control Message Protocol is also working on the Internet layer and provides a way to determine the health of a network or a specific link. Commands like ping, traceroute and other network management tools utilize ICMP to send echo packets to remote hosts. With ICMP it is possible to determine whether a remote system is online, how fast it responds and if intermediary systems support the communication.
Many attacks exploited the features of ICMP in forms of denial-of-service (DoS) attacks like ping floods or smurf attacks. This has affected the way how networks handle ICMP today, resulting in many limiting the use of ICMP or the throughput rate of this protocol.
The Internet Group Management Protocol or IGMP allows systems to support multicasting in an IPv4 network. Multicast management on IPv6 networks is handled by Multicast Listener Discovery (MLD). Both protocols support the transmission of data to multiple specific recipients.
Link
The link layer defines the networking methods within the scope of the local network link on which hosts communicate. This layer includes the protocols used to describe the local network topology and the interfaces needed for the transmission of Internet layer datagrams to next-neighbor hosts.
ARP or Address Resolution Protocol is enabling the interoperability of logical and physical addressing of interfaces. It resolves IP addresses into Medica Access Control (MAC) addresses.
Traffic on a network is directed from its source to its destination using MAC addresses. ARP uses broadcasting and caching to perform the intended purpose. If the cache doesn’t contain the necessary information, an ARP request is broadcasted into the network.
Conclusion
TCP/IP follows principles that helped the model to adapt to new requirements and stay meaningful. Robustness, Adaptability and Continuous Evolution are core values mentioned in the defining RFCs of the Internet Protocol Suite.
But TCP/IP vulnerabilities are numerous and range from improperly implemented stacks in operating systems to buffer overflows, denial-of-service or spoofing attacks. It is also subject to passive attacks via monitoring traffic patterns or sniffing the content of communication by man-in-the-middle attacks. Deep knowledge of TCP/IP is a must for any security professional to mitigate the risk of attacks.
The Internet Protocol Suite is the underlying fabric of the internet and I could only provide a quick overview in this posting. Understanding the basics of networking should be in the interests of any Internet user.