Kick back with us and dig into a selection of the best articles, code, and projects we found this past month.
Spring4Shell: The Internet security disaster that wasn’t
People were naturally concerned when a researcher published a proof-of-concept exploit that could remotely exploit the popular Spring framework. Without much information available and no CVE assigned, people were unable to determine their exposure. Some security companies jumped on the hype train and warned of imminent danger that “could ruin the internet” to sell their snake oil. A great write-up on the worst side of the security industry, selling services through fear, comes from Arstechnica. >read<
KA-SAT Network cyber-attack overview
In our March Roundup we had an article about thousands of KA-SAT terminals that stopped working for an unknown reason. The provider ViaSat has now released an incident report on the cyber-attack against the network. Spoiler alert, the misconfiguration in a VPN appliance was used to gain the initial foothold into the system. >read<
Graph-based firewall analysis
It is good practice to review firewall rules after changes to identify potential attack paths that have been missed. The use of a graph-based approach can help tremendously to visualize the rules and find gaps in the configuration. >read<

Display of data using yEd
Distributed tcpdump for Kubernetes
The toolbox of any security professional includes capturing network traffic with tcpdump or Wireshark. Gathering the network traffic of distriubuted workloads in cloud environments has been a challenge for forensic analysis. PacketStreamer (GitHub) utilizes sensors to collect network packets on remote hosts and enables the collection of traffic activities on a large number of target systems. >read<
Authorization in a microservices world
Alexander Lolis wrote a great blog post about different authorization approaches and what a flexible mechanism could look like. >read<
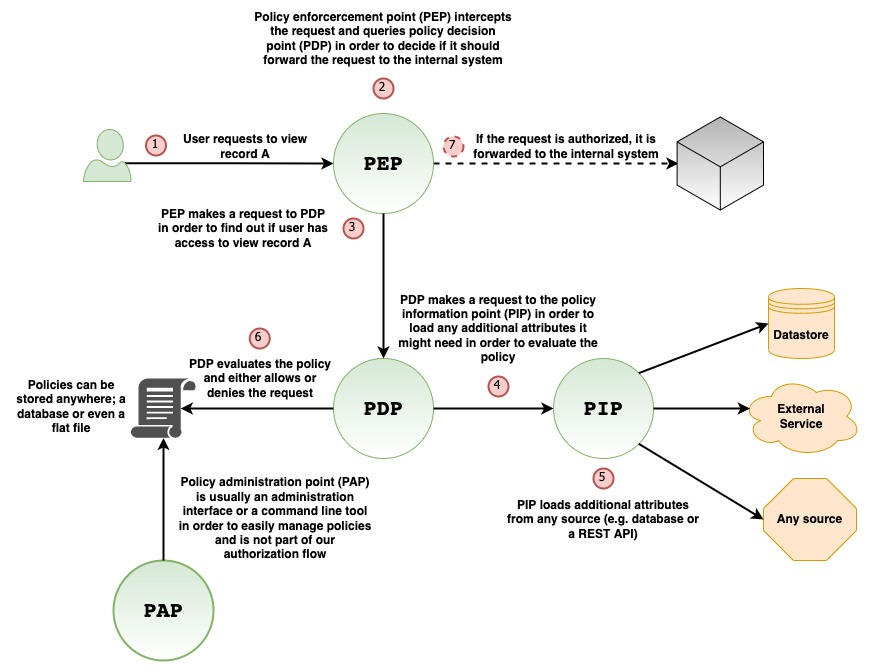
Authorization mechanism
AWS patch against Log4j introduces new security holes
We are still seeing the fallout from the worst Christmas present in years, Log4Shell. A hot patch system introduced to address Log4Shell has been exploited to escape containers and take over the underlying host in AWS. Unit 42 (Paloalto networks) researchers identified the severe security issues within the AWS patching solution. >read<
Introduction to CSRF: How can a cookie get you hacked?
Cookies serve three purposes: session management, personalization, and tracking. They are assistants to webservers that work in conjunction with the browser to make your life easier. If, however, the web application relies only on cookies to manage sessions, the attacker can perform the infamous CSRF attack. Check out the following article for an introduction to CSRF attacks >read<